TLDR: It was possible to bypass Windows UAC and gain administrative privileges by abusing the Properties of any network adapter. This is applicable in organizations where administrators allow non-privileged users to alter their TCP/IP Settings.
What is UAC?
User Account Control (UAC) serves as a security control within the Windows Operating System. Its primary function is to ensure that any new process is initially set to run within the security parameters of a non-privileged account, regardless of the user initiating it, even if they are administrators. The approach here is that we shouldn't depend entirely on the user's identity to decide if certain actions should be allowed.
UAC bypass?
UAC Bypass essentially is a way or a technique for achieving privilege escalation, whether through manual intervention or script execution, and it can be exploited through several methods.
Background
Altering a computer's IP address typically requires administrative privileges due to its potential impact on network connectivity and security. However, there are valid situations where standard users may require adjustments to their TCP/IP settings. This could occur if DHCP is disabled, during frequent travels when encountering network issues, or when network operators need to conduct troubleshooting and testing.
In these scenarios, administrators typically employ group policies or Endpoint Privilege Management (EPM) solutions like BeyondTrust Privileged Access or CyberArk EPM to authorize such actions. And in the case of granting elevated access to Network Properties, this is accomplished through COM elevation whitelisting.
COM elevations are typically initiated from Explorer when an integrated task necessitates administrator rights. Explorer and other processes such as dllhost utilize COM to execute the tasks with admin privileges, avoiding the need to elevate Explorer itself. Every COM class has a unique identifier, called a CLSID, that is used to launch the task. And the CLSID of the network adapter properties is {7007ACD1-3202-11D1-AAD2-00805FC1270E}.
This configuration isn't standard by default on Windows, and not all companies adopt this setup. Nonetheless, we've encountered this issue in numerous companies and successfully demonstrated the escalation abuse path successfully.
Abusing this to escalate privileges
I will demonstrate how one can leverage this configuration to open an elevated command prompt with administrator privileges.
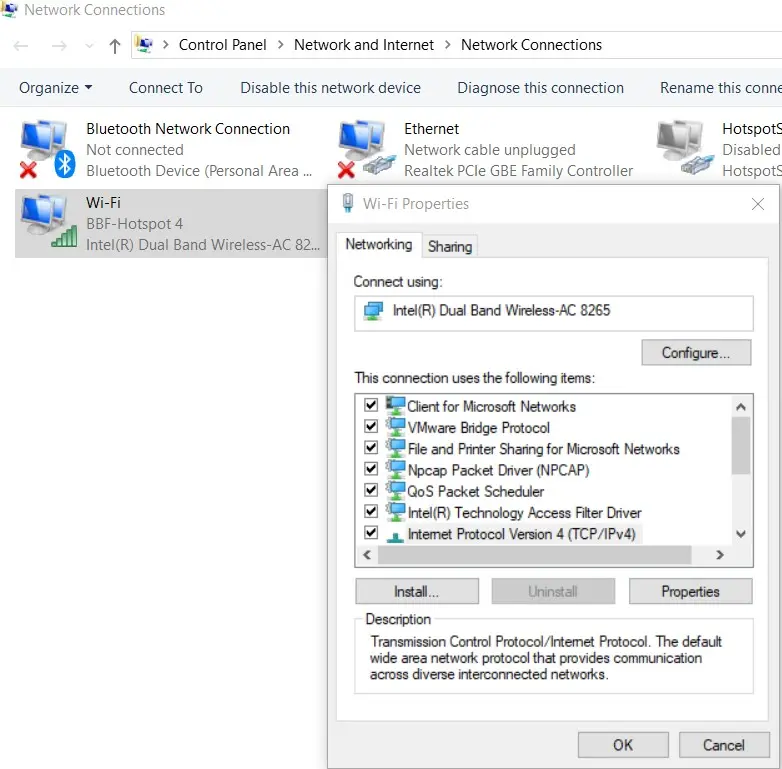
- In the Start menu, go to "View Network Connections", and right click on your selected network adapter, e.g. "Wi-Fi" adapter and select Properties.
At this point, if you didn't receive the UAC elevation prompt, you should be good. Otherwise, your company restricts standard users from changing their network settings.
- We can verify that the newly created process runs in an elevated state from the Task Manager. Look for the following process command line:
DllHost.exe /Processid:{7007ACD1-3202-11D1-AAD2-00805FC1270E}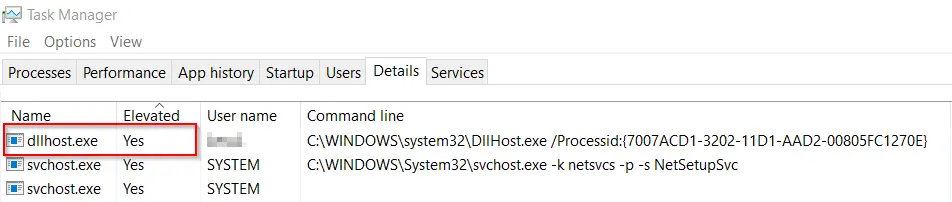
- Next, go to the TCP/IPv4 setting, then access the advanced menu located at the bottom. Navigate to the final tab labeled "WINS" and select "Import LMHOSTS".
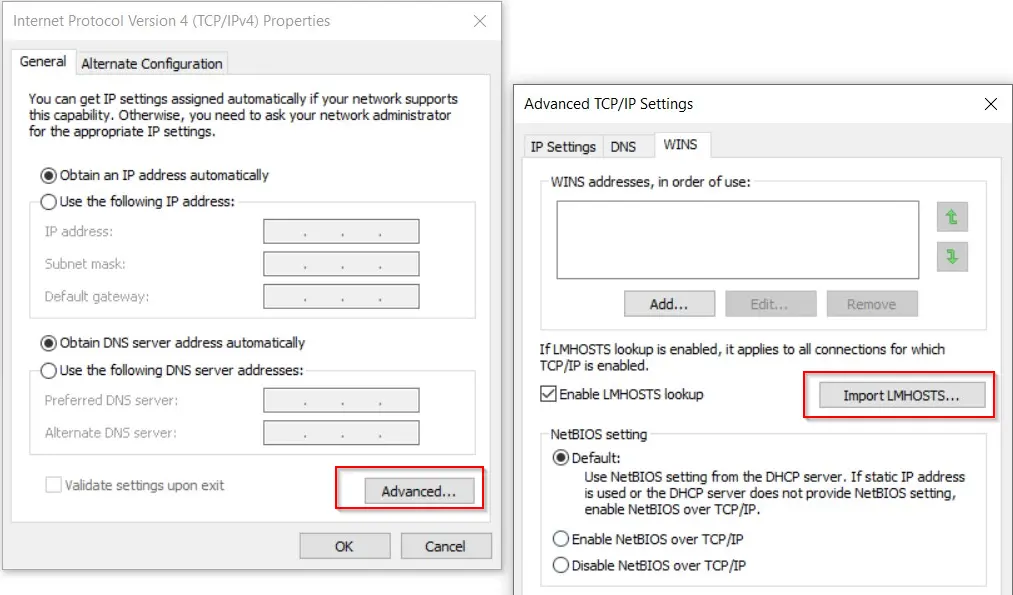
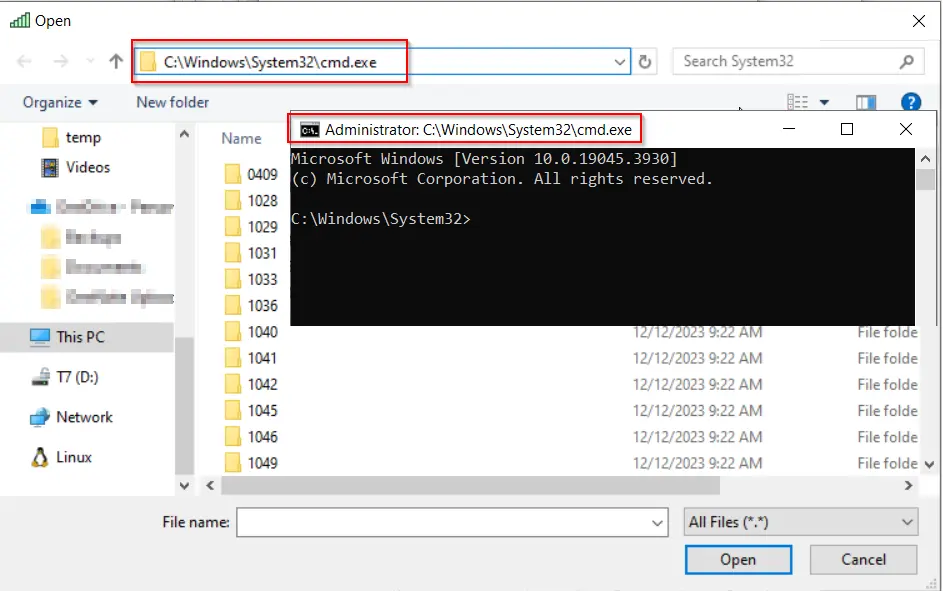
- Once the Explorer window is open, you can navigate to the System32 folder and view various Windows system files, including applications like cmd.exe. By opening the cmd.exe, you'll launch an administrator command prompt window. Congratulations, you've successfully executed UAC bypass privilege escalation and gained administrator rights!
Powershell Check
I was looking into scripting the mentioned technique in command prompt or PowerShell rather than GUI to achieve the same result. Unfortunately, at the time of writing this article, I haven't discovered a programmatic approach to exploit this UAC bypass and launch an elevated Command Prompt.
The following PowerShell snippet will open the properties of the default Wi-Fi adapter, launching an elevated dllhost process similar to how you would in the graphical interface.
$nic = "Wi-Fi"
$shell = New-Object -com 'Shell.Application'
$NETWORK_CONNECTIONS = 0x31
($shell.Namespace($NETWORK_CONNECTIONS).Items()|Where{$_.Name -eq $nic}).InvokeVerb('Properties')Conclusion
In conclusion, exploring the bypassing of User Account Control (UAC) via network adapter properties highlights the importance of addressing potential security gaps in Windows systems, especially when administrators loosen security boundaries to offer flexible solutions for end users.
Organizations should be particularly mindful when granting elevated permissions for such properties changes, as such allowances can inadvertently expose systems to heightened risks of unauthorized privilege escalation and exploitation. By leveraging EPM solutions with finely-tuned policies, organizations can effectively control and monitor user privileges, mitigating the risk of unauthorized access and enhancing overall endpoints security.